About
|
making spammers' lives more difficult
Contents
- How it works
- How well it works
- Some results
How it works
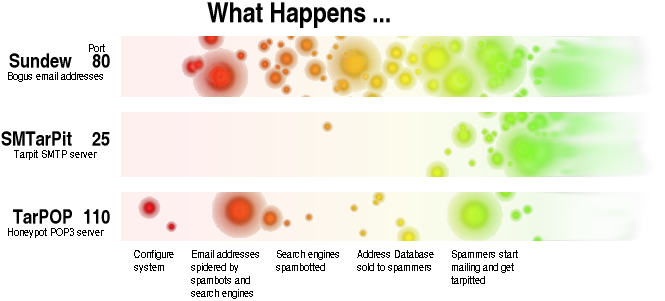
You don't have to do much to help with this. If you just use Sundew to set up a bogus email honeypot, you will have helped to poison the spammer's databased with useless addresses and you can even to that with a Windows machine. If you configure the honeypot on a non-Windows machine and you don't use port 25 to receive your email, you can also set up the SMTP tarpit.
Once the spammers have the email addresses that point to your firewall, you will start to get spam tarpitting and wasting spammer's time. Also, if you dont't use a POP3 server on port 110, you can set up a honeypot on that - this will keep the hackers off the streets.
The rough outline of what happens when you set up Sundew is in the flow chart on the right.
* The configuration instruction for Sundew are in the Perl script itself.
Get a free domain name from somewhere like DynDNS and then configure your honeypot so that it has the same domain name. That way, their 'bot' will think that the addresses are real because they match up with the domain name.
You will need to point a link to the bogus email address honeypot though. This link should be in a web page that is already spidered by the search engines. All it need be is an image link of one pixel - the same colour as the background of the page. The idea is that the link is not likely to be clicked on by any normal user but being written into the HTML code of the page, the search engine's web crawler will see it and follow it through.
Every six months or so, you can re-seed your honeypot with a new donain name and a new set of bogus email addresses. Rename the virtual host file for it in your web server and your 'invisible' link in the web page and there will be some more email addresses to work their way into the spammer's databases.
SMTarPit is easy to configure. There are a number of parameters that allow you to make it difficult for the spammer to decide if your SMTP server is actually a tarpit. If they run their mail sender program, it will tarpit the server - one connection I had spend 30 days trying to send email before it gave up. If they try logging into it with telnet on port 25, then the tarpit will act like a honeypot instead with shorter delays. You can alter tha mount of time it takes to do various things and configure it to behave differently at different times of the day. It also has a mechanism that prevents it from clogging up your server.
You can only use the tarpit if you have a reason for people to send you spam so you should already have a DynDNS or other domain name database entry pointing at your firewall. All you have to do is configure SMTarPit and sit back and watch the logs grow with spammers if you decide to log them.
TarPop is really there for the cracker or for port scans. It will keep them occupied so that we can learn something about them and whilst we are learning, they are not on the streets, mugging old ladies. Again, you need a DNS entry somewhere so that they can log on on port 110 (POP3) and try to do something. You don't have to run TarPop to make the rest of it work but it can be entertaining.
How well it works
This is how effective the combined efforts of the Sundew spambot honeypot and SMTarPit SMTP Tarpit are. Note that this graph used to be updated regularly but since then, the tarpit has been saturated so there is no point updating it)...
Breakdown by week . . . Week
StartingT i m e . . . Total
SecondsTotal
(Hours)Longest
(Hours)*Hits
from:<>rcpt
to:4 Apr 2005
16,465,660 4,573 43 4023 9 2,690 11 Apr 2005
19,115,812 5,309 43 8536 42 1,875 18 Apr 2005
16,942,413 4,706 60 6843 105 1,822 25 Apr 2005
20,109,432 5,585 39 8045 554 990 2 May 2005
24,162,991 6,711 49 14144 2,821 416 9 May 2005
22,759,262 6,322 119 12576 1,250 1,031 * A hit is a new connectsion
** 'mail from:<>' is a null sender which is not allowed on this server. (Might be spam.)
Day of week . . .
H
i
t
s
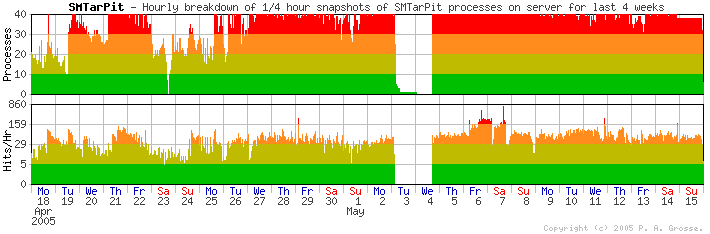
Day Mon Tue Wed Thu Fri Sat Sun Per cent 10 12 12 15 20 19 12 created at: 02:01:13 on Mon 16 thMay 2005 This shows how many processes the SMTarPit has had - it is set to a maximum of 35 - handling politely the final 5 up to the 40 in total that the superserver will hand it.
Some Results
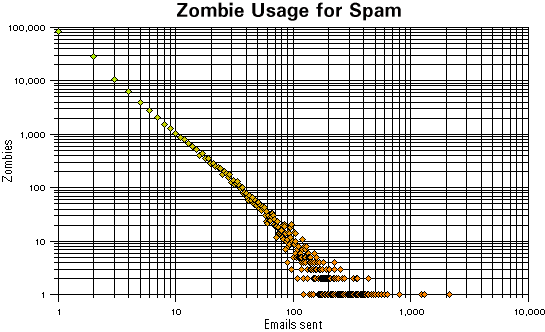
I have taken the log files of connections that made it over a period of time and runs to 644,419 attempts to send an email. This covers 154,773 unique IP addresses of which 84,869 sent only 1 email. The proportion of addresses that sent only one email was 55 per cent but the quantity of mail they account for was only 13 per cent.
In the graph, you can see that some addresses were responsible for sending out many emails - the largest number of mails from one address being 2,146.
Have fun.
Paul Grosse
email paul-grosse at ntlworld dot com